A little known fact about running Azure AD Connect is that is defaults to a weaker than necessary TLS version (version 1.0). Or rather, the host OS Windows Server 2012 (incl R2) does. It perhaps isn’t the end of life as we know it but it’s unnecessary since both Azure AD and Windows Server 2012 (R2) has it enabled and is ready for us to make use of. All we have to do is to force Windows to always use it.
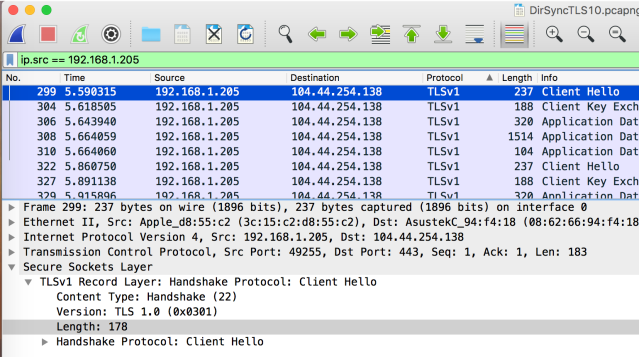
Using Wireshark to see what the default behavior is (192.168.1.205) is my Azure AD Connect Server and 104.44.254.138 is Microsoft Azure. We clearly see that Client Hello (our server) is asking for TLSv1.
The much needed registry key, that enables us to force Windows Server to always use TLS 1.2 is “SchUseStrongCrypto”=dword:00000001 as documented here: Prerequisites for Azure AD Connect (scroll down to the section titled Enable TLS 1.2 for Azure AD Connect. The key (DWORD) goes into HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v4.0.30319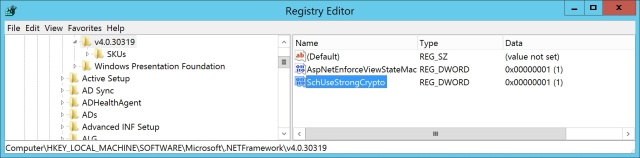
Reboot the Azure AD Connect server and let’s have another look:
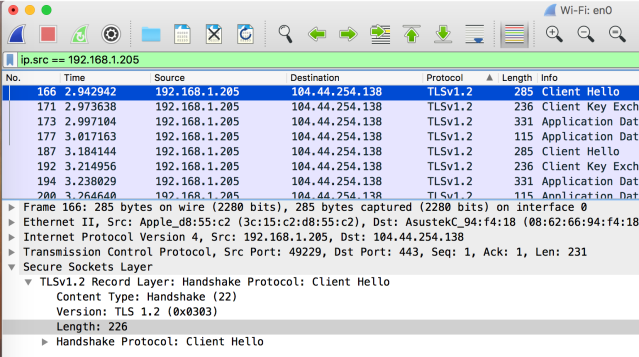
YEY!!


